
Regardless of whether companies operate their ERP systems in the cloud or locally, there is no such thing as one hundred percent security. However, the risk of attacks can be minimized with various adjustments.86 percent of companies in Germany have recently suffered damage from cyber attacks, according to Bitkom research. And the trend is rising: according to the industry association, the damage caused by blackmail, IT failures or the disruption of operational processes has risen by 358% since 2019.
Despite this threat situation, however, many ERP providers and users (still) seem to be taking the issue of security lightly: In the "Cloud ERP 2021" study by IDG Research, 20 percent of the companies surveyed stated that cloud ERP security was not important to them, or not important at all. Perhaps this thinking dates back to the time when most companies operated their ERP systems locally on their own server. But the ERP world has changed: Today, more and more applications are moving to the cloud. They are therefore accessible from the outside and also offer a larger attack surface for hackers.
On the other hand, established cloud providers such as Amazon Web Services (AWS) or Microsoft Azure have a very high security standard that is difficult to achieve, especially for a medium-sized company with an on-premises solution.
The multicloud challenge
In terms of security, it is therefore not so important whether companies operate their ERP systems locally or in the cloud. Rather, the complexity of the entire application landscape is decisive. This is because most companies combine their ERP systems with applications from specialized providers from different clouds that are connected to each other via interfaces. And the trend is rising: according to the American cyber security provider Vectra AI, almost two thirds of all companies worldwide now book new AWS services on a weekly basis. However, this increasing and constantly changing networking of different applications and systems harbors the risk of gaps and errors, which hackers can unfortunately also exploit in the worst-case scenario.
According to the IDG study "Cloud Security 2021", 39% of companies with 500 to 999 employees in the DACH region reported economic losses in the last twelve months due to attacks on the cloud services they use. For companies with fewer than 500 or at least 1,000 employees, the figure is still 32 percent.
The widespread use of agile methods and continuous delivery (CD) in the adaptation and development of (ERP) systems also harbors security risks. Ever shorter cycles and release times reduce the time available for sufficient testing and experience in the field. This can become a problem not only for the manufacturers, but also for the user companies. This is because they often have to ensure that the updates work smoothly and securely across the entire multi-cloud environment within very tight timeframes. Not forgetting possible security gaps in open source libraries (e.g. log4j), which are also used in many commercial software solutions today.
Log4shell
In mid-December, the Java security vulnerability "Log4Shell" shook Germany's IT departments and suddenly brought the issue of security to the attention of ERP users. The vulnerability, which appeared in the widely used Log4j logging library for Java applications, is considered to be the largest security vulnerability in the history of the Internet. The problem: Log4shell makes some of the world's most popular applications and services vulnerable, as the Log4j framework is used on millions of servers. The server vulnerability that has now been discovered allows attackers to execute their own program code on the target system and thus compromise the server. The BSI initially classified the IT threat situation for business processes and applications as extremely critical in December and issued the highest warning level "red". The situation has since eased somewhat and the warning level has therefore been lowered from "red" to "yellow". Further information can be obtained directly from the BSI at: https://www.bsi.bund.de/SharedDocs/Cybersicherheitswarnungen/DE/2021/2021-549177-1032.html
Human security risk
Whether it's phishing emails, insecure passwords or carelessly connecting the office laptop to infected hardware - even the most secure technology cannot prevent users from making mistakes. The coronavirus crisis in particular, in which the living room suddenly became the workplace for many employees, acted as a fire accelerator: according to Bitkom, since the start of the pandemic, 59% of companies with employees working from home have experienced IT security incidents in connection with working from home. In 24% of these companies, these incidents were even frequent.
Damage caused by working from home
The fact that many employees have increasingly worked from home during the pandemic has contributed to an enormous increase in economic losses due to cybercrime. According to the Cologne Institute for Economic Research, around 52.5 billion euros in losses were attributable to home office attacks in 2020, 31 billion euros more than before the pandemic.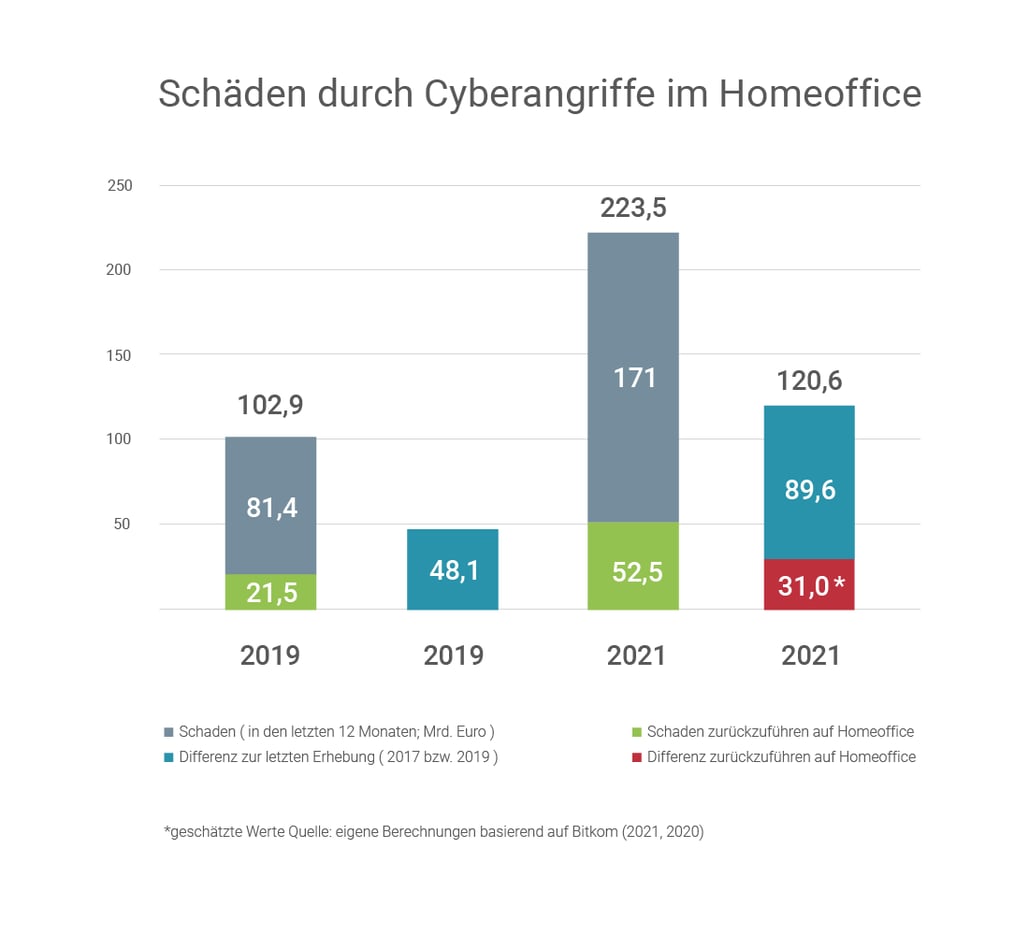
Working safely at home
In view of the fact that working from home will remain an integral part of the working world even after the pandemic, companies should make adjustments here if necessary: regular security training, secure passwords and clearly defined user and authorization rules should also be standard when working from home.
Up-to-date authentication processes also define exactly which data in an ERP system an employee is only allowed to read and which they are also allowed to change or link to others. This significantly reduces the risk of data theft or manipulation by employees. Mobile workstations should also have up-to-date end-to-end encryption or, even better, multi-factor authentication.
Technical protection
On the technical side, there are a whole range of other measures to protect ERP systems from attacks:
Companies that obtain their ERP solution from the cloud should first carefully study the provider's security concept. Key questions include: Is the data transferred between the cloud server and the user's end device encrypted? Are the servers located in a certified data center so that regular fail-safe and encrypted data storage, access controls, system monitoring, fire protection and redundancy are ensured?
Certifications such as the ISO9000 series for quality management or the ISO27001 certification for secure data centers usually provide information in this context. Providers who do not like to show their cards when it comes to security issues should be treated with caution.
For processes that involve data exchange between different platforms or between on-premises and cloud solutions, the user companies themselves are required to pay attention to regular updates and new features and to keep an eye on their impact on the IT landscape. Regular security audits and penetration tests should also be standard practice.
In order to detect leaks such as log4shell in good time, software providers should regularly check their open source components for vulnerabilities and check the libraries used (dependency checks) for vulnerable code. Training developers in the creation of secure code is also strongly recommended.
For extensive hybrid ERP landscapes, some companies also rely on central SIEM solutions (SIEM = Security Information and Event Management). These monitor ERP systems automatically and in real time. This enables them to detect threats immediately and thus offer additional protection for IT operations and compliance. Control mechanisms, reports and tools for automated compliance and maintenance monitoring provide additional relief for IT security experts in companies.
Securing the cloud, but the right way
In order to be prepared for emergencies, not only large companies but also many SMEs now rely on cloud backup systems. They store particularly sensitive backup data there or even mirror their entire infrastructure. We recommend having such solutions designed and managed by specialists. Supplemented by regular training for administrators and regular security checks.
Small carelessness with major consequences
What is actually intended as a safety measure can also turn out to be the opposite if done incorrectly. One of the best-known examples is the case of the car rental company Buchbinder. The company's IT department had conscientiously created daily backups on an external server. However, a port that allows data transfers via SMB (Server Message Block) was fatal. Around three million pieces of customer data, including addresses and telephone numbers of celebrities, top politicians, embassy staff and employees of federal ministries, were thus available unprotected on a server for weeks. All an attacker had to do was enter the correct IP address into the browser. Around ten terabytes of data could then be downloaded. No password was required.
Just in case
In an emergency, clear responsibilities are the be-all and end-all. A constantly updated security concept and an emergency list with the relevant contact details should therefore always be up-to-date and available to all employees who work with the ERP and all connected systems. Ideally, emergency plans should not only cover the company's own operations, but also include suppliers and important customers, for example in the form of specific instructions. A list of alternative suppliers is also recommended if existing ones are no longer available.
An emergency plan is a living document. It must be updated regularly and adapted to changing conditions. And: even the best emergency plan is useless if employees cannot find it in an emergency. The document should therefore be stored in a central location that is easily accessible to all employees.
Despite all caution, absolute security is not possible in an ERP world in which hybrid and networked systems are the norm. But with the right measures, the success rate of hackers can at least be greatly reduced. And in an emergency, this not only saves nerves, but also a lot of money.
Safety checklist
- Regular security training, password hygiene and clearly defined user and authorization rules are just as important in the home office as they are in the office.
- If your employees work on the move, make sure they have up-to-date end-to-end encryption or multi-factor authentication.
- Take a close look at the security concept of your cloud provider: Certifications such as the ISO9000 series for quality management or ISO27001 certification for secure data centers are standard these days.
- You are responsible for processes relating to data exchange between different platforms and providers. Keep an eye on regular updates and new features as well as their impact on the IT landscape and ensure regular risk assessments. Equally important: security audits and penetration tests.
- Software providers should regularly check their open source components for vulnerabilities and keep an eye on the libraries used (dependency checks) for vulnerable code.
- Central SIEM solutions can provide support for hybrid ERP landscapes. They monitor your ERP systems automatically and in real time and detect threats immediately.
- Backup solutions should always be designed and managed by specialists. Regular security checks and further training for administrators are also recommended.
- If the worst comes to the worst, make sure you always have an up-to-date safety concept and an emergency list with all the important contact details.


